Architecture Overview
VeilNet Architecture Overview
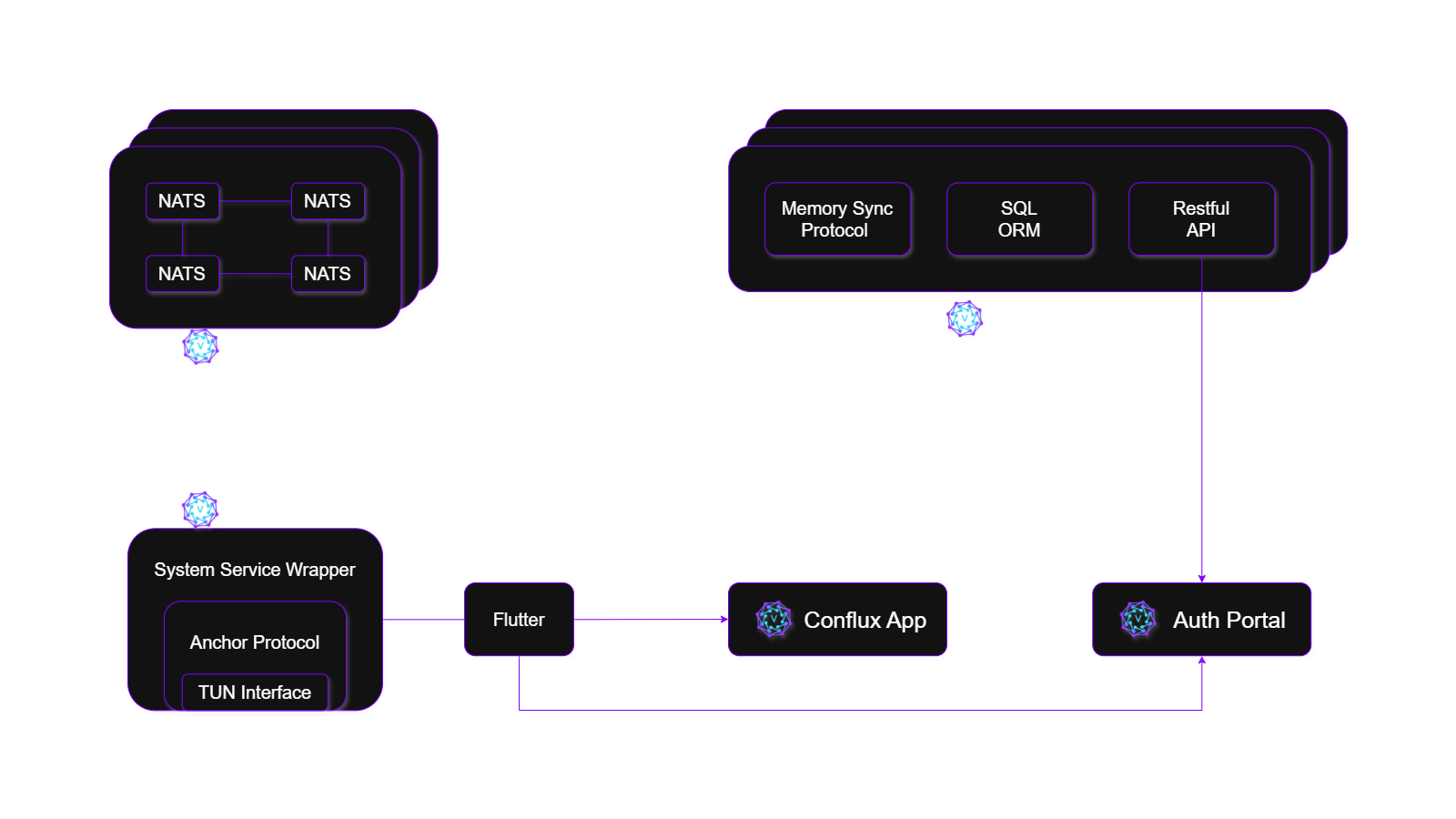
VeilNet is an identity-native overlay network designed for distributed systems, agentic workloads, and sovereign infrastructure.
Its architecture is intentionally decomposed into three tightly integrated but strictly separated components: Master, Guardian, and Conflux.
This separation enforces a clean distinction between coordination, control, and data movement, avoiding centralized datapaths or application-layer trust chains.
Master
Control-Channel Fabric (NATS Super Cluster)
Master is a globally distributed NATS super cluster that forms VeilNet’s control-channel fabric.
Its role is limited to coordination, signaling, and message distribution. Master provides a reliable, low-latency control channel that enables Conflux nodes and Guardian services to exchange control-plane information while remaining strictly separate from data-plane traffic.
Master is used by Conflux nodes and Guardian services to:
- Exchange encrypted control and coordination messages
- Propagate topology, liveness, and health signals
- Coordinate negotiation of ephemeral, multi-hop routing paths
- Distribute control intents and orchestration signals
Master does not execute routing logic or learning algorithms.
Instead, it supports distributed decision-making performed by Conflux nodes.
Distributed Reinforcement Learning Support
Reinforcement learning (RL) is executed locally within Conflux nodes. Each node maintains its own learning state and policy based on partial, local observations.
Master supports this process by acting as a control-plane communication substrate, allowing Conflux nodes to:
- Publish and subscribe to topology and reachability updates
- Share summarized path and health signals with peers
- Receive coordination messages relevant to path exploration and convergence
These signals provide the contextual inputs required for RL-driven path selection without centralizing learning or policy evaluation.
Guardian Interaction
Access to the Master control channel is explicitly authorized by Guardian.
Guardian issues cryptographically verifiable authorization that allows a Conflux node to:
- Join specific control-channel subjects
- Publish or subscribe to defined classes of control messages
- Receive remote administrative commands
Guardian can issue remote administrative commands to Conflux nodes via Master, such as:
- Querying local Conflux state and local network context (e.g., interface status, routes, peer/session state, local health signals)
- Applying taints / quarantine markers to restrict participation or isolate a node from specific realms/peers
- Forcing key/material invalidation and triggering disconnect / teardown
- Shutting down or disabling the Conflux service (graceful stop or hard revoke, depending on policy)
These commands are administrative and enforcement-oriented (control-plane), and do not constitute path computation or data-plane routing control.
Guardian
Authentication & Authorization Control Plane
Guardian is VeilNet’s authentication and authorization (AuthN/AuthZ) control plane.
It is responsible for establishing and validating identity, trust, and authority across the VeilNet control plane, without participating in routing, coordination, or data-plane traffic.
Guardian operates as a cryptographic authority, not as a stateful orchestration or coordination service.
It does not maintain distributed runtime state related to routing, learning, or control-plane coordination.
Guardian is responsible for:
- Authenticating Conflux nodes and control-plane participants
- Authorizing access to VeilNet control-plane resources
- Issuing short-lived Conflux credentials used to access the Master control channel
- Establishing mutual TLS (mTLS) identities for secure control-plane communication
- Defining network isolation boundaries derived from authenticated identity context, where supported
Network isolation is determined at network join time, based on authenticated identity attributes and Guardian-issued authority. This allows isolation and trust boundaries to be enforced at the network layer rather than through application-level mechanisms.
Guardian determines who may join the network, under which identity, and which isolated network context they are permitted to participate in, but does not observe, influence, or mediate data-plane behavior.
Guardian does not participate in path selection, reinforcement learning, coordination, or packet forwarding.
Its role ends once identity, authorization, and isolation context have been cryptographically established.
Conflux
Connector, Distributed Control Agent, and Data Plane
Conflux runs on endpoints—servers, containers, edge devices, workloads—and can be deployed either as a system-level service or embedded directly into applications at the code level.
In both modes, Conflux acts as the connector between the execution environment and the VeilNet fabric, and is responsible for all data-plane operations.
Each Conflux instance joins a Realm, enforcing identity, isolation, and policy at the packet boundary, forming the entirety of VeilNet’s data plane.
Conflux operates as a distributed control and execution agent, combining routing intelligence, cryptographic session management, and packet forwarding within a single node.
Core Components
- Integration Layer / System Wrapper Provides lifecycle management and access to local networking context. When embedded, this layer exposes programmatic interfaces for initializing Conflux, attaching traffic sources/sinks, and controlling runtime behavior from application code.
- Anchor Protocol: VeilNet’s transport protocol responsible for:
- Establishing encrypted communication channels
- Negotiating and maintaining ephemeral, multi-hop paths
- Managing post-quantum–secure key exchange and session state
- Binding cryptographic sessions to authenticated node identity
- Packet Interface (TUN or Embedded I/O)
- TUN-based interface for system-level deployment
- Direct packet or stream interfaces for embedded, in-process integration This allows applications to inject and receive traffic without relying on OS-level network configuration where not required.
Distributed Routing and Learning
Each Conflux instance functions as an independent reinforcement learning (RL) agent for routing and path selection.
Using local observations and control-plane signals received via Master, Conflux nodes:
- Evaluate candidate peers and paths
- Select, rotate, and retire multi-hop routes
- Establish, refresh, and invalidate encrypted sessions
- Adapt forwarding behavior in response to network dynamics and failures
Learning and decision-making are fully decentralized. There is no global routing table, centralized controller, or shared policy model. Each Conflux node converges independently based on partial visibility and asynchronous updates.
Data Transmission
Conflux authenticates peers, establishes cryptographic sessions, encrypts packets, and forwards traffic directly between endpoints.
Data-plane operation does not rely on:
- Fixed gateways
- Public IP exposure
- Centralized relays or proxies
All encryption, session management, routing decisions, and packet forwarding occur locally within Conflux instances, whether deployed as standalone services or embedded directly into application runtimes.
